The Dark Side of the Cloud
Nima Hazar, MSc | Oct 22, 2014 | Tech Computing Apps
Cloud computing, or simply ‘cloud’, is a broad, over-used term that refers to the offering of data storage, computing services or resources over the internet. However, it is not cloud's vague definition, but rather its characteristics that make it especially appealing to emerging and growing businesses. Cloud computing is highly flexible to its users’ needs and is incredibly scalable. It allows businesses to focus on their product rather than the infrastructure, and helps them get their applications up and running faster while avoiding upfront costs.
Cloud computing is the result of the evolution of existing technologies and paradigms. The main enabling technology is Virtualization. The two things you need to know about virtualization software are that one, it separates the physical device (hardware) from the computing device - for example, you can have multiple virtual machines running their own operating systems on a shared physical device - and two, it introduces an additional layer, the virtualization layer, that changes the relationship between the operating system and the underlying hardware.
Through these technologies, cloud computing is able to offer flexibility and scalability without requiring its users to have a deep knowledge of said technologies. It serves the needs of its customers in different forms: IaaS (Infrastructure as a service), PaaS (platform as a service), SaaS (Software as a service) and Private Clouds.
Knowing this, it shouldn’t come as a surprise to see the rate at which businesses and startups are adapting to cloud. The exponentially increasing interest in cloud computing has started something resembling a war between cloud providers. One example is the recent price cut announced by Google, which was followed closely by Amazon. Today, finding a giant tech company that does not provide cloud services is like finding a needle in a haystack. Amazon Web Services, Google Cloud platform, Microsoft Azure, IBM Cloud (aka SoftLayer), Oracle Cloud, are all trying to find a share in this booming market. Cloud computing and services have become the backbone fuelling startups and Fortune 500 companies alike. A prime example is Netflix, whose interface operates on Amazon Web Services (AWS) and shows no signs of leaving.
Clouds, of course, have unique challenges. The CSA (Cloud Security Alliance) has compiled a list of the top nine cloud computing threats, called “The Notorious Nine”. The first on the list is data leakage, followed by data loss. Service traffic hijacking (XSS attacks), insecure interfaces, denial of service (DoS) attacks and insufficient due diligence are all members of The Notorious Nine. The message of The Notorious Nine is clear: clouds have all the security issues of internet hosting or in-house services, and more. Here, we keep our focus on cloud-specific security risks.
Let us start with multitenancy because, well, the idea of having multiple, usually unrelated users sharing the same computing resources sounds alarmingly daunting. Multitenancy exploits are very troublesome because the compromise of (or by) one customer can lead to the compromise of another. It means that regardless of how well you manage your security, as long as another customer’s system is vulnerable, yours is too. The (other) bad news: researchers already have shown that it is possible to peek into another tenant’s memory or completely take over another tenant’s computing resources.
Even virtualization itself must be properly configured, managed and secured. Remember how virtualization brought flexibility and scalability to cloud by adding a layer between the OS and the hardware? Well this also opens the door to a new family of exploits targeting the virtual server hosts and guests. There are various types of virtual exploits and unfortunately they are all relatively unknown to most cloud customers.
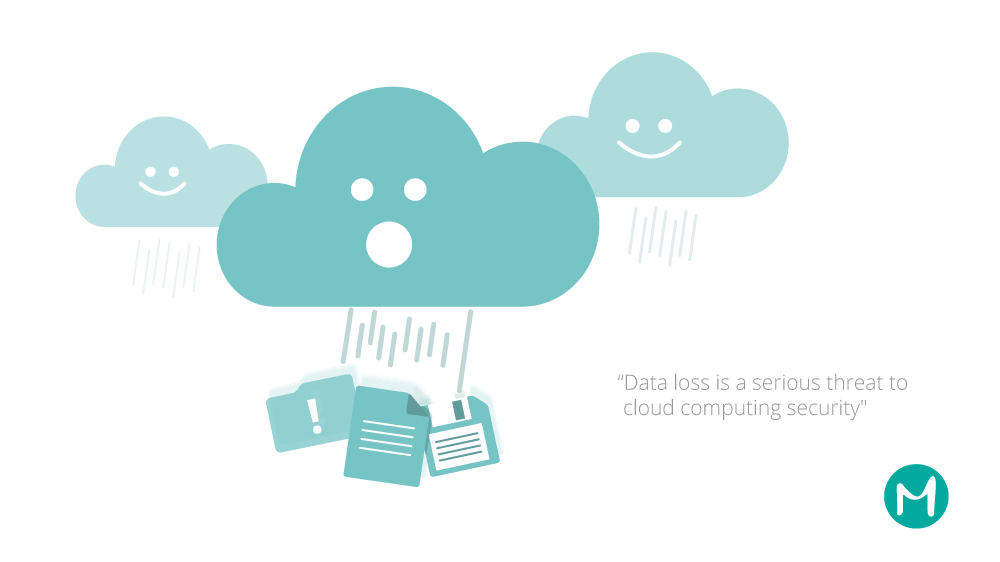
Another threat in a cloud computing environment is data loss. A hacker can tap into your system and delete your data, or even more easily, the cloud provider could fail and your data could be permanently lost . Losing data usually has serious consequences: you may lose your valuable customers and your potential market could lose trust in you. In cases where data should be stored in compliance with regulations such as HIPAA the consequences could be far more severe. Logically you may think about backing up your data yourself, however opting to keep these backups will then increase your risk of data breaches. Solving one problem further complicates another.
The last threat that we cover in this article may come as a surprise: it happens when organizations choose the cloud vendor without fully understanding the contractual issues over liability or transparency, or even ownership of the data. Owning the data provides better legal protection to cloud vendors. As crazy as it may sound, you need to ensure you have done extensive due diligence before embracing the cloud, or you may lose ownership of your own data.
Flexibility and scalability have greatly increased with the maturity of cloud computing, and so has the complexity of cloud security. This means that more measures need to be considered or the system will be vulnerable. (You may have heard of the XSS attack on Amazon in 2010 that let attackers hijack credentials to the site, or the 6.5 million LinkedIn passwords that were leaked online in 2012.) The good news however, is that cloud security has finally grabbed the spotlight and vendors are being forced to step in before more catastrophes emerge.
In our next post on cloud security, we will review some measures for ensuring the security of your system and your data in cloud.
References:
The Notorious Nine: Cloud Computing Top Threats in 2013
Everyone Loves the Cloud Price Wars — For Now
9 top threats to cloud computing security
The 5 cloud risks you have to stop ignoring
Cloud computing enables business scalability and flexibility